API Sprawl Is a Data Governance Problem: Fix It by Putting Elementrix Behind Your Gateway.
Integrating Elementrix Behind Your API Gateway: A Modern Architecture for Governed Data Delivery :
Enterprise teams have largely standardized on API Gateways (Apigee, Kong, WSO2, etc.) to control ingress: authentication, rate limiting, and traffic management. That’s necessary, but it is not sufficient when APIs become the primary path for operational data consumption.
If you’ve ever shipped “one more endpoint” because a new consumer needed a slightly different payload, or watched upstream systems buckle under real-time fan-out traffic, you’ve already felt the gap: gateways manage traffic—they don’t manage governed data delivery.
This post outlines a clean integration pattern: keep your existing API Gateway, and place Elementrix behind it as the governed data delivery layer—built to enforce data-product contracts, approvals, entitlements, auditing, and dynamic response shaping without multiplying services.
Why API Gateways Don’t Solve Data Delivery
Most enterprises face three critical challenges when delivering data:
API gateways excel at:
- Authentication and identity verification
- Rate limiting and quota enforcement
- Routing and traffic management
But data delivery breaks down when:
- Governance is bolted on late and enforced inconsistently
- Schema changes propagate across downstream services and consumers
- Consumer-specific payloads cause API sprawl
- Upstream systems are queried in real time for every request (creating fragility and cost)
In practice, teams end up with a growing “API factory” that is expensive to maintain and risky to change.
The Pattern: Gateway for Edge Enforcement, Elementrix
for Governed Data Delivery.
The integration principle is straightforward:
- Your API Gateway remains the edge: auth, throttling, routing
- Elementrix becomes the governed data delivery layer: data product contracts, policy enforcement, consumer-specific shaping, resilience via decoupling
Instead of building dozens of bespoke services or endpoints, you define and govern data products and let runtime delivery be driven by policy.
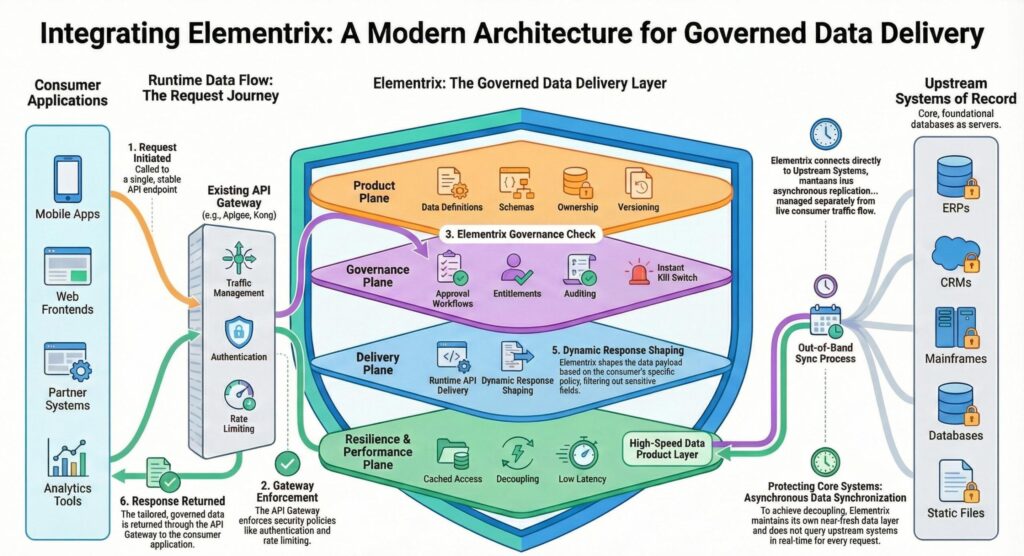
Architecture Overview (What Each Layer Owns)
1) Consumer Applications
Mobile apps, web frontends, partner systems, analytics tools.
They call a stable API contract through the gateway—without needing to know upstream topology or governance rules.
2) Existing API Gateway (Apigee / Kong / WSO2)
Owns:
- Authentication / token validation
- Rate limiting / quotas
- Traffic management
- Routing to Elementrix runtime
The gateway validates “who is calling” and applies standard edge controls.
3) Elementrix: The Governed Data Delivery Layer
Elementrix operates across four planes:
1- Product Plane
- Data definitions
- Schemas
- Ownership
- Versioning
2- Governance Plane
- Approval workflows
- Entitlements
- Auditing
- Instant kill switch
2- Delivery Plane
- Runtime API delivery
- Dynamic response shaping (policy-driven field filtering)
4- Resilience & Performance Plane
- Cached access
- Decoupling from upstream
- Predictable low-latency delivery via a high-speed data product layer
4) Upstream Systems of Record
ERPs, CRMs, databases, mainframes, static files.
Elementrix protects these systems by serving most runtime requests from a near-fresh layer maintained by asynchronous sync—not by querying upstream for every call.
Runtime Request Journey (Step-by-Step)
Step 1: Consumer calls a stable endpoint (Gateway)
Consumers call a standard endpoint such as:
- /data/customer-profile
- /data/order-status
Step 2: Gateway enforces edge policies
Typical enforcement includes:
- JWT/OAuth2/mTLS validation
- Rate limits and burst control
- Basic threat protection rules
Then the gateway routes the request to Elementrix, forwarding identity context (claims, consumer ID, scopes).
Step 3: Elementrix runs governance checks
This is where governed data delivery differs from gateway-only architectures.
Elementrix evaluates:
- Is this consumer entitled to the data product?
- Is approval required, and has it been granted?
- What fields are permitted for this consumer?
- Should access be blocked (kill switch, incident response)?
- What is the audit footprint for this transaction?
Step 4: Elementrix reads from the high-speed data product layer
Instead of calling upstream systems in real time, Elementrix serves from a decoupled layer maintained asynchronously.
This is a major reliability win: upstream downtime doesn’t necessarily become consumer downtime.
Step 5: Elementrix shapes the response dynamically
Elementrix tailors the payload based on consumer policy:
- Removes sensitive fields
- Projects only required fields for mobile vs. web
- Applies partner-specific views
- Reduces over-fetching
Outcome: one data product, multiple governed views, without creating new endpoints for each consumer.
Step 6: Response returns through the gateway to the consumer
The gateway remains the consistent entry/exit point for telemetry, metrics, and standard response behavior.
The Out-of-Band Sync Process
(How Upstream Systems Stay Protected)
A key design decision is separating: Live consumer traffic from
Upstream synchronization
Elementrix maintains near-fresh data through asynchronous sync patterns such as:
- CDC-based replication (ideal for transactional sources)
- Scheduled extracts (common for legacy constraints)
- File-based ingestion (common for SaaS exports and mainframe dumps)
This protects systems of record from being hammered by runtime requests and gives you explicit control over freshness SLAs.
What Developers Actually Implement
Below are the real build surfaces most teams deliver with this pattern. The examples are illustrative (technology-agnostic) and meant to reflect structure and intent.
1) Define a Data Product (Contract + Ownership + Versioning)
dataProduct:
name: CustomerProfile
version: v1
owner: “Retail Banking Domain”
steward: “Data Steward – Customer”
freshnessSLA: “≤ 2 minutes”
schema:
customer_id: string
full_name: string
phone: string
national_id: string
segment: string
balances:
current: number
available: number
2) Configure Governance (Approvals + Entitlements + Audit)
accessPolicy:
product: CustomerProfile:v1
consumer: “PartnerA-App”
approvalRequired: true
allowedFields:
– customer_id
– full_name
– segment
deniedFields:
– national_id
– phone
– balances
audit: true
killSwitch:
enabled: true
3) Configure Response Shaping (Consumer-Specific Views)
Instead of creating CustomerProfileForMobile, CustomerProfileForPartner, CustomerProfileForAnalytics, you shape views at runtime through policy.
4) Tune Resilience & Performance
Teams typically define:
- cache strategy and TTL by product
- fallback behavior when sync is delayed
- latency SLOs by consumer tier
- enforcement when freshness SLA is violated (serve stale vs fail closed)
Minimal Change Gateway Wiring
Most gateway teams only need to:
- Add a route mapping (e.g., /data/* → elementrix-runtime)
- Propagate identity context (claims/scopes/consumer ID)
- Keep existing gateway policies intact (rate limits, auth, WAF, logging)
This makes the adoption path incremental—not a re-platform.
Operational Considerations That Matter
Freshness contracts must be explicit
If you decouple runtime reads from upstream systems, define:
- freshness SLA per product
- acceptable staleness per consumer
- behavior on SLA breach
Schema evolution should be intentional
Use product versions:
- additive change → compatible within same version where possible
- breaking change → major version
- enforce deprecation windows
Audit and incident response should be first-class
Governed delivery is not only about access control—it’s also about operational control:
- audit logs: who accessed what, when, with which fields
- kill switch: immediate revocation without redeployments
Why This Pattern Works
This approach creates a clear separation of concerns:
- API Gateway: edge security + traffic management
- Elementrix: governed data delivery (contracts, approvals, entitlements, audit, shaping, resilience)
The result is:
- fewer endpoints to maintain
- safer distribution (least privilege, auditable)
- better reliability (upstream decoupling)
- faster consumer onboarding (policy-driven delivery)
Developer Checklist Appendix
Use this checklist to implement the “Gateway + Elementrix” pattern with production discipline.
-
A) API Gateway Setup
- Define routing: /data/* → elementrix-runtime
- Ensure auth validation at gateway (JWT/OAuth2/mTLS)
- Forward identity context (consumer ID, roles, scopes, correlation ID)
- Apply rate limits and quotas by consumer tier
- Preserve distributed tracing headers (traceparent or equivalent)
-
B) Data Product Definition (Product Plane)
- Assign clear owner and steward
- Define schema contract (fields, types, semantics)
- Declare versioning approach (v1/v2 + deprecation policy)
- Document freshness SLA and retention expectations
- Define canonical identifiers and domain keys
-
C) Governance Configuration (Governance Plane)
- Define entitlement rules (who can request what)
- Implement approval workflows (who approves, SLAs, escalation)
- Enforce field-level permissions (allowed + denied lists)
- Enable auditing (who/what/when/fields delivered)
- Configure kill switch for consumers and/or products
-
D) Sync & Decoupling (Out-of-Band Process)
- Select sync model: CDC vs scheduled extract vs file ingestion
- Define sync frequency and acceptable staleness
- Monitor lag metrics and alert thresholds
- Define “sync down” behavior (serve stale vs fail closed)
- Validate data quality checks post-sync (row counts, null rates, drift)
-
E) Runtime Delivery & Shaping (Delivery Plane)
- Implement response shaping policies per consumer
- Confirm sensitive field filtering (PII/PCI/PHI) by default
- Validate payload size constraints for mobile clients
- Ensure consistent error contracts (status codes, error envelope)
- Add policy tests for each consumer view
-
F) Performance & Reliability (Resilience Plane)
- Configure caching strategy per product (TTL, invalidation)
- Define SLOs: p95 latency, availability, freshness compliance
- Validate capacity under peak loads (load tests)
- Ensure fallback strategy and graceful degradation paths
- Implement end-to-end observability (logs, metrics, traces)
-
G) Security & Compliance
- Encrypt data at rest and in transit end-to-end
- Define secrets management for sync connectors
- Implement periodic access reviews (entitlement recertification)
- Ensure audit logs are immutable and retained per policy
- Perform data classification mapping (PII tiers, masking rules)
Ready to Solve Your API Sprawl?


