Data Monetization Without Data Chaos: Build an External Data Marketplace with Elementrix
Most enterprises have valuable data that partners would pay to access. What stops them from turning it into a repeatable revenue stream is not demand—it’s operational risk. The moment you distribute data externally, you inherit responsibilities that ad-hoc sharing methods cannot handle at scale: licensing enforcement, tenant isolation, privacy controls, metering and billing, SLAs, auditability, and rapid revocation.
Many teams begin with “quick wins” such as CSV exports, shared storage locations, partner-specific APIs, or a one-off integration service. Those approaches can work for one partner, but they break when you try to support multiple partners, tiered plans, different data products, and compliance oversight. The cost becomes exponential: every partner turns into custom logic, custom pipelines, and custom exceptions.
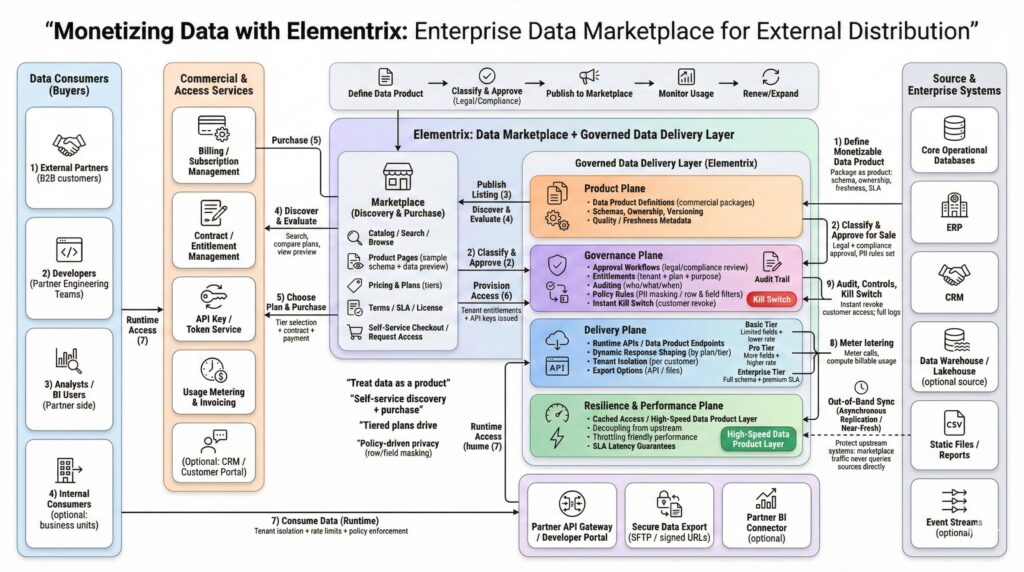
This use case shows a scalable alternative: treat data as a product and distribute it through an enterprise data marketplace powered by Elementrix. Elementrix combines marketplace discovery and purchase with a governed data delivery layer that enforces commercial and compliance controls at runtime.
What “data monetization” really requires
Selling data is not the same as exposing data. A monetizable data program must answer several hard questions consistently.
Here are the most common pain points:
- No enforceable contracts at runtime. A contract exists on paper, but the delivery mechanism can’t enforce it.
- Plan/tier chaos. Each tier becomes a new dataset or pipeline, multiplying maintenance.
- Privacy inconsistencies. Masking and row filters vary by team, partner, or tool.
- No defensible usage metering. You can’t invoice reliably without trusted measurement.
- Weak revocation. When risk appears, you can’t shut off access immediately.
- Operational load on source systems. Partners indirectly create “read storms” on production systems.
If any of these are true, scaling beyond a few partners is difficult and risky.
The solution pattern: Elementrix as “Marketplace + Governed Data Delivery”
The architecture works because it combines two capabilities that are often implemented separately (and therefore fail separately).
Elementrix provides:
- A Marketplace layer for discovery, evaluation, pricing, terms, and purchase workflows.
- A Governed data delivery layer for runtime access enforcement, policy-driven privacy, tenant isolation, and SLA-backed performance.
The important part is the connection between the two. Buyers don’t just purchase “access”; they purchase a governed data product with a tier and entitlements that are enforced automatically whenever they consume data.
Who participates in this ecosystem
External distribution always involves multiple personas and operational functions. The platform needs to support them without turning everything into manual coordination.
Buyer-side consumers
- External partners (B2B customers) consuming business datasets or operational feeds
- Partner engineering teams integrating against APIs and tool endpoints
- Partner analysts / BI users consuming via governed extracts or BI connectors
- Optional internal business units using the same marketplace for intra-company sharing
Seller-side operational functions
- Commercial & access services, such as:
- billing / subscription management
- contract and entitlement management
- API key/token issuance
- usage metering and invoicing
- optional CRM/customer portal integration
The end-to-end lifecycle: from product definition to recurring revenue
A scalable data marketplace must support a repeatable product lifecycle. In this use case, the lifecycle is designed to be self-service where possible and controlled where required.
1) Define a monetizable data product
You package a dataset as a product with clear commercial and operational expectations.
That typically includes:
- schema and contract definition
- ownership and stewardship
- versioning and change policy
- freshness and quality metadata
- SLA targets (availability, latency, update frequency)
This step is where you shift from “tables” to “products.”
2) Classify and approve the product for sale
Before publishing externally, products are reviewed by legal/compliance and security. The goal is to codify the rules as policy, not as custom code.
Approval commonly includes:
- licensing and usage restrictions
- privacy policy rules (PII masking, row-level filters)
- approved consumption modes (API, files, both)
- audit and retention requirements
3) Publish the listing to the marketplace
Once approved, the product becomes a marketplace listing that buyers can discover and evaluate.
Listings usually contain:
- product description and business value
- schema documentation and sample preview
- pricing plans and tier comparisons
- terms, SLA, and license details
This reduces sales friction without exposing sensitive content.
4) Buyers discover and evaluate
Buyers browse, search, and compare offerings. The platform provides enough information to evaluate fit while keeping access governed until purchase and entitlement provisioning are complete.
This is where marketplaces replace ad-hoc sales enablement PDFs and repeated enablement calls.
5) Buyers choose a plan and purchase
A marketplace must support tiered commercial packaging without creating separate datasets per tier.
Common plan structures include:
- Basic tier: limited fields, lower rate limits, standard support
- Pro tier: more fields, higher rate limits, broader use rights
- Enterprise tier: full schema access, premium SLAs, stronger support commitments
The “tier” should drive delivery behavior through policy—rather than branching pipelines.
6) Provision access (entitlements + API keys)
After purchase, access is provisioned automatically. This is where commercial state turns into runtime enforcement.
Provisioning typically includes:
- tenant entitlements bound to the purchased plan
- API keys/tokens issued via an API key/token service
- rate limits aligned with tier
- access start/end dates aligned with subscriptions
7) Runtime consumption through governed endpoints
Buyers consume data via runtime access paths, with tenant isolation and policy enforcement.
Typical delivery options include:
- partner API gateway / developer portal for API-based consumption
- secure file exports (SFTP, signed URLs) for extract-based consumption
- optional partner BI connectors for analyst workflows
8) Metering and billing
The system measures billable usage so invoicing is defensible and consistent.
Metering commonly tracks:
- API calls, payload size, and query volume
- exported file counts and download volume
- tier-based thresholds and overages
9) Audit, controls, and instant revocation
External distribution needs operational control. When misuse or risk appears, access must be stopped immediately without waiting for new deployments.
This includes:
- full audit trail (who accessed what, when, and under which plan)
- policy enforcement logs (masking/filter rules applied)
- kill switch capability to revoke customer access instantly
How Elementrix enforces monetization at runtime
The reason this pattern scales is because Elementrix turns “commercial intent” into runtime behavior.
At runtime, Elementrix can enforce:
- Tenant isolation: each partner’s access is isolated and scoped
- Policy-driven privacy: field masking and row filters applied per plan and per customer
- Dynamic response shaping: payloads differ by tier without creating separate datasets
- Performance guarantees: cached, decoupled reads reduce upstream dependency
- Auditability: every access is logged with context, including product version and entitlement state
This is what turns external distribution from “a set of integrations” into “a product platform.”
Why this avoids the typical marketplace failures
Most “data marketplace” efforts fail because they stop at discovery. They publish a catalog, but delivery still happens through bespoke exports and partner-specific pipelines. That creates a disconnect: the marketplace sells something the platform cannot reliably enforce.
This architecture avoids that by binding the marketplace to governed delivery. Plans, entitlements, privacy policies, metering, and revocation are not separate systems stitched together manually—they are part of the runtime path.
Developer Checklist Appendix: External Data Marketplace with Elementrix
Data product packaging
- Define schema, ownership, freshness metadata, and SLA expectations
- Establish versioning and deprecation policies
- Create tier-friendly product boundaries (fields and shapes that can vary safely)
Legal/compliance approval workflow
- Implement classification and approval gates before publishing
- Encode privacy rules as policy (masking/row filters)
- Attach terms, license, and SLA to product listings
Marketplace and purchase workflow
- Support product pages, previews, and clear tier comparisons
- Implement self-service checkout / request access
- Integrate subscription and contract systems (if separate)
Provisioning and runtime delivery
- Issue API keys/tokens and bind them to tenant entitlements
- Enforce plan-based limits (rate limits, field access, payload constraints)
- Provide delivery channels (API endpoints, secure exports, optional BI connectors)
Metering and invoicing
- Meter calls and usage in a billable way
- Track tier thresholds and overage logic
- Produce invoice-ready usage records
Audit and control
- Log access with customer, plan, product version, and policy decisions
- Enable rapid revocation (kill switch) with clear authority and process
- Monitor anomalies (unexpected query patterns, burst usage, policy violations)
Lorem, ipsum dolor sit amet consectetur adipisicing elit. Nam obcaecati laudantium recusandae, debitis eum voluptatem ad, illo voluptatibus temporibus odio provident.


